Help customers solve various data security problems.
Demand Analysis
-
-
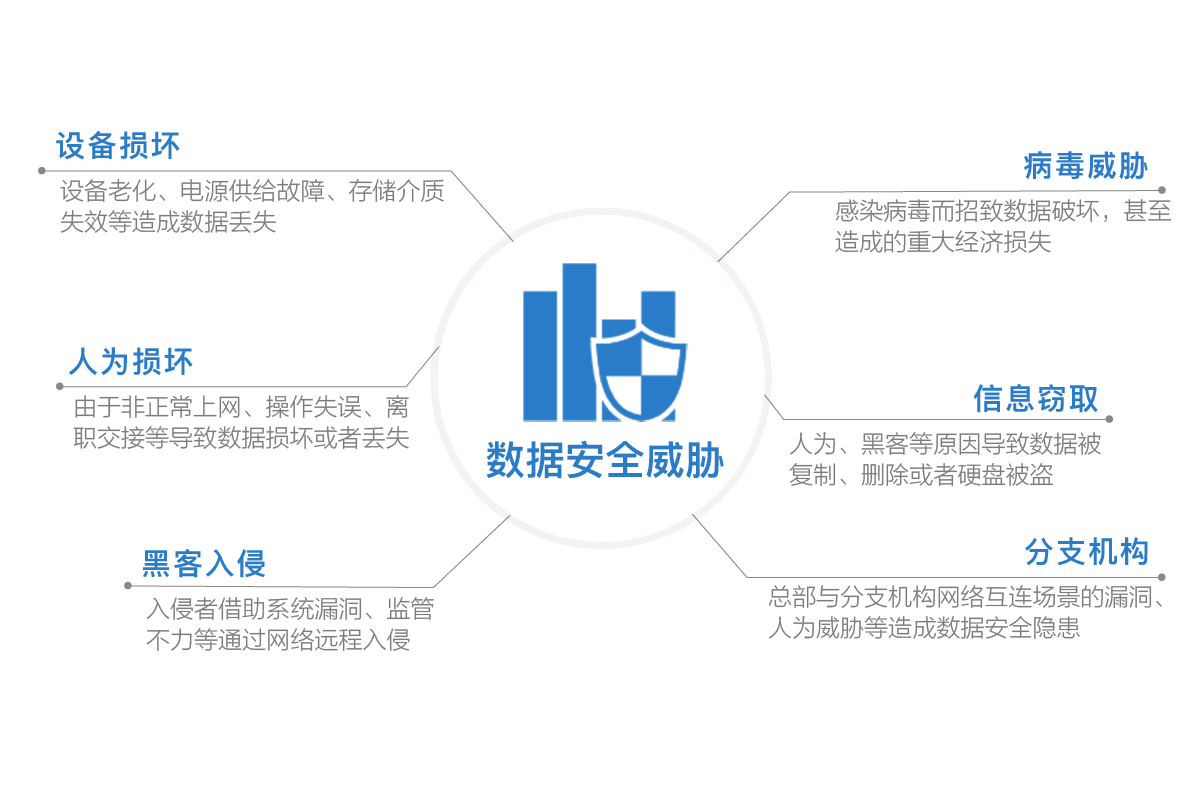
In the Internet age, corporate data is the company's most important asset. In an open network environment, building an enterprise-level security environment is essential.
Enterprise development business is complicated, and security risks are difficult to identify
The malicious person has invaded the inside of the network, and you still don't know
Safe operation and maintenance is more complicated, and the work is heavy and inefficient.
The stable and efficient operation of Internet security firewall hardware and software has just been needed.
The online behavior of enterprise employees has many invisible risks. For data security, the Internet needs to be visible and controllable.
Solution
-
Help customers solve various data security problems and improve data privacy protection.
Internet Border Security
Data security portal network import and export is the top priority of data security. Based on customer needs, we will build a network security environment such as egress firewall, PC mobile VPN access, employee online behavior management, and link load balancing to protect enterprise Internet security.
Terminal access security
Terminal access is the entry point to the data center and the most important security threshold. Based on the security considerations of terminal access, setting relevant permissions, transmission and log review are essential security measures.
Data Center Protection
The data center can be said to be the most important asset of an intranet. Various business data, financial information, applications, etc. are stored here. Based on the needs of data center security, it addresses issues such as security visualization, future expansion of data centers, network connection protection, and interaction security between devices and data centers.
Branch Security
Branch offices in different locations require secure, efficient, and stable access to the internal network. VPN is a solution for building a private network on a public network. Build your own VPN environment based on cost and demand.
DMZ
Build a DMZ zone to store enterprise Web servers, Ftp servers, VPN servers, and forums. Some enterprises must disclose their access to the network environment. By creating a screened subnet, the trusted network is distinguished from the untrusted network and isolated. It is more resistant to continuous attacks and protects important data resources even if some areas are not working. In the future, we can optimize the Guangcheng network according to the demand and improve the access speed of the DMZ area.
Data Security Related Brands
-

HuaWei
A leader in the network security industry
Fortune 500 companies
Quality products, quality technology -

DAS-Security
Global Network Security 500
G20 core security support unit
Cloud security, big data security leading brand -

360
One of China's Internet security companies
China's first magic quadrant to be selected for terminal protection platform
14 years old safe brand -

Safedog
Domestic well-known Internet security brand
Focus on (cloud) server security
Cloud & Client Cloud Security Management Platform
Hot Products
Application Scenario
-
Internet Security
-
Website Security
-
WAN Security
-
Data Center
-
Safety Isolation
-
Campus Network
-
Branch Network
-
Internet Security
Realize the visibility of more elements in the user, behavior, business and other dimensions, and comprehensively analyze the visual data to achieve risk location and graphical threat display. At the same time, all aspects of the hacker chain are continuously detected. Using cloud sandbox technology and big data threat intelligence analysis platform, it can respond to security events in a timely and accurate manner and reduce the threat impact to a lower level.
-
-
Website Security
For the protection of user Web service websites, the static defense system based on feature update in the past will be given the cloud security detection capability by convincing the next generation firewall to achieve active and active defense. Once a device discovers new and unknown threats, it can quickly pass through the cloud. Update and implement network-wide interception within 24 hours. Combined with the cloud automation website security anomaly monitoring technology, users can get notifications and warnings within a few minutes when there are security incidents such as vulnerabilities, tampering, black chains, and hanging horses.
-

-
WAN Security Awareness
It can not only improve the security protection capability of the WAN, but also help users to understand the security risks of the branch in real time, avoiding the weak points of security construction in the branch office and becoming an intrusion short board, so as to realize the centralized management and operation and maintenance automation.
-
-
Data Center Security
Data center security can be effectively supplemented to solve the problem of planning only firewalls in the early stage of design, lack of comprehensive security defense and detection technology. It mainly includes three aspects: application layer security hardening, enhanced security detection technology, and simplified security management to ensure data center information security in complex business environments.
-

-
Safety Isolation
The data center is divided into regions according to different security levels to achieve hierarchical, focused and comprehensive protection and access control. It effectively solves the problems of on-line deployment, new business and daily management strategies, and poor visibility in traditional firewalls.
-

-
Campus Network Security
Construct a comprehensive security defense system for the campus network, providing multi-dimensional, continuous and stable security. Precision defense: a powerful knowledge base / reputation library system, intelligent policy definition. Network-wide defense: Unknown threat protection based on big data and security situational awareness. Continuous security: Continuous analysis of global live network traffic, rapid response to zero-day attacks.
-

-
Branch Network Security
For the mass branches and business outlets, an end-to-end interconnection system with fast online, comprehensive security and centralized management will be constructed. Security all-in-one: Build comprehensive security and reduce deployment costs. Simplified management: Massive branches are quickly launched and unified certification management. Boost business: business outlets online, industry applications and advertising push.
-





